Malbuster Writeup
Intro:
Malbuster is a premium room located on Try Hack Me. It is designed around the idea of being tasked with analyzing a sample from your SOC team.
link to room: https://tryhackme.com/r/room/malbuster
Room description:
Scenario
“You are currently working as a Malware Reverse Engineer for your organisation. Your team acts as a support for the SOC team when detections of unknown binaries occur. One of the SOC analysts triaged an alert triggered by binaries with unusual behaviour. Your task is to analyse the binaries detected by your SOC team and provide enough information to assist them in remediating the threat.”
Flags for this challenge will not be given directly but the steps for finding them are described, there are many ways to find some of these flags and I encourage all who read this to try it on their own first.
Analysis:
We can find our samples in C:\Users\Administrator\Desktop\Samples
We are given specfic tasks/questions to anwser, lets start analyzing.
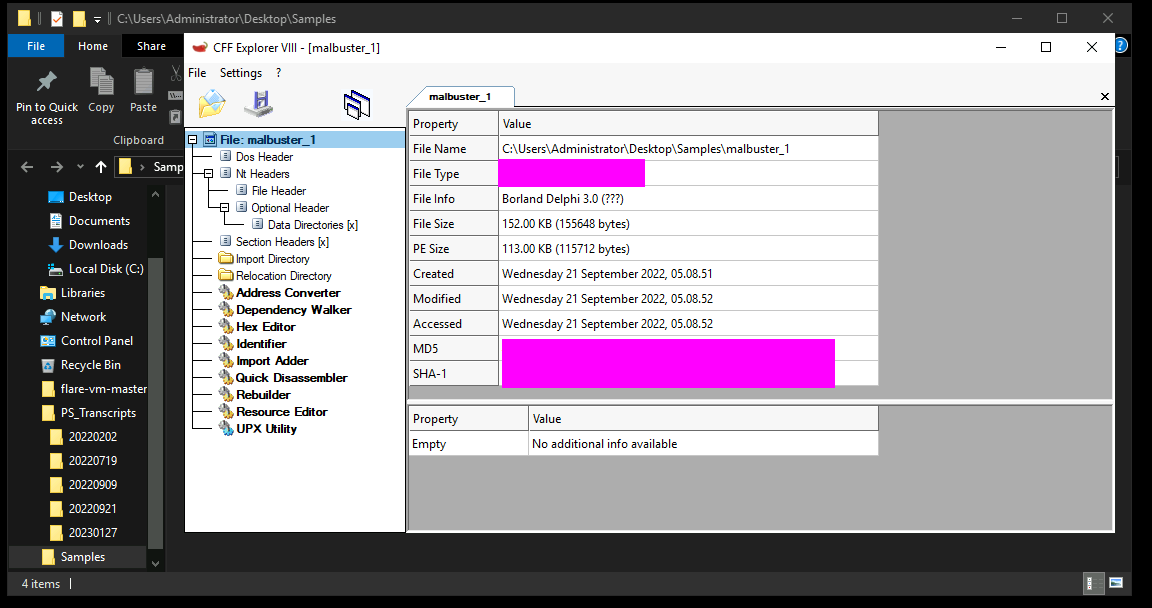
- 1: Based on the ARCHITECTURE of the binary, is malbuster_1 a 32-bit or a 64-bit application? (32-bit/64-bit):
- 2: What is the MD5 hash of malbuster_1?
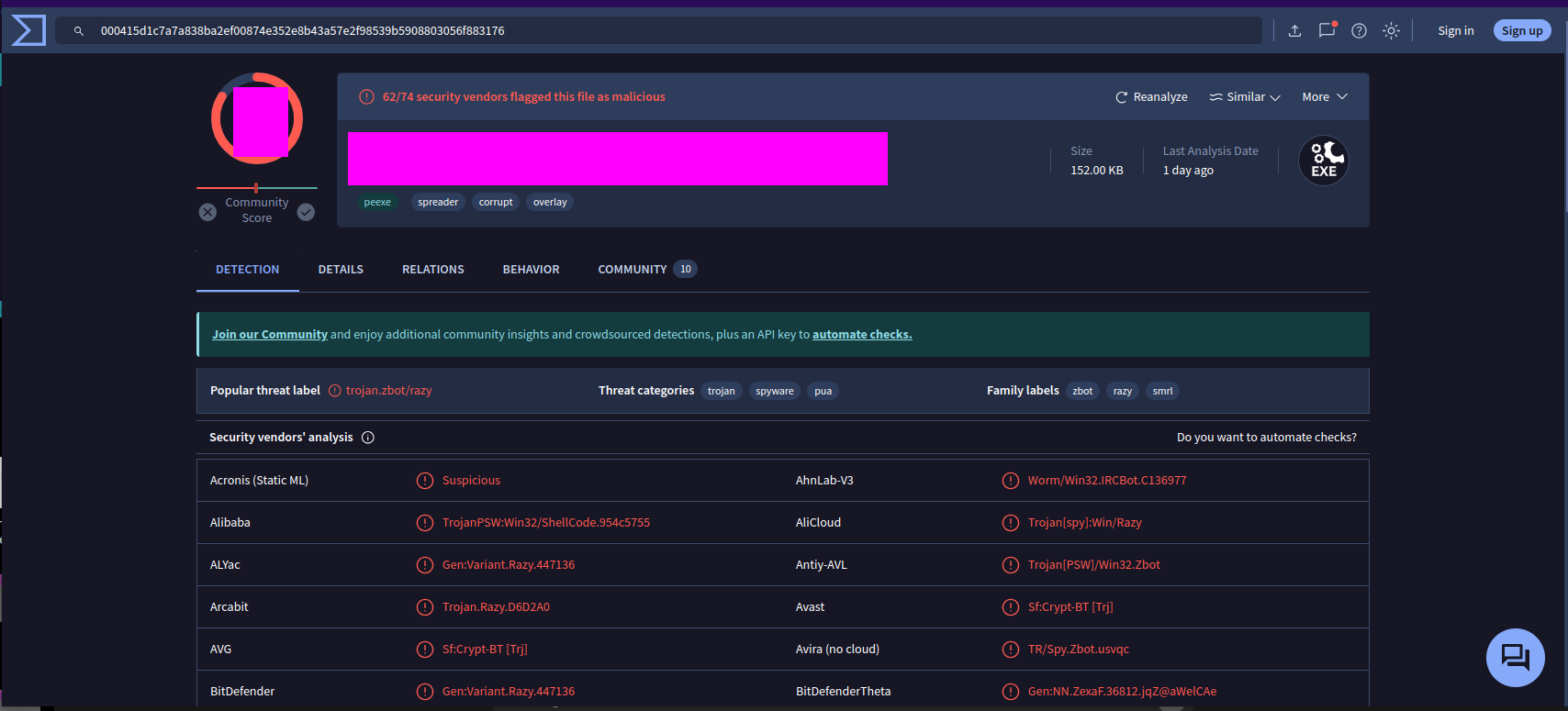
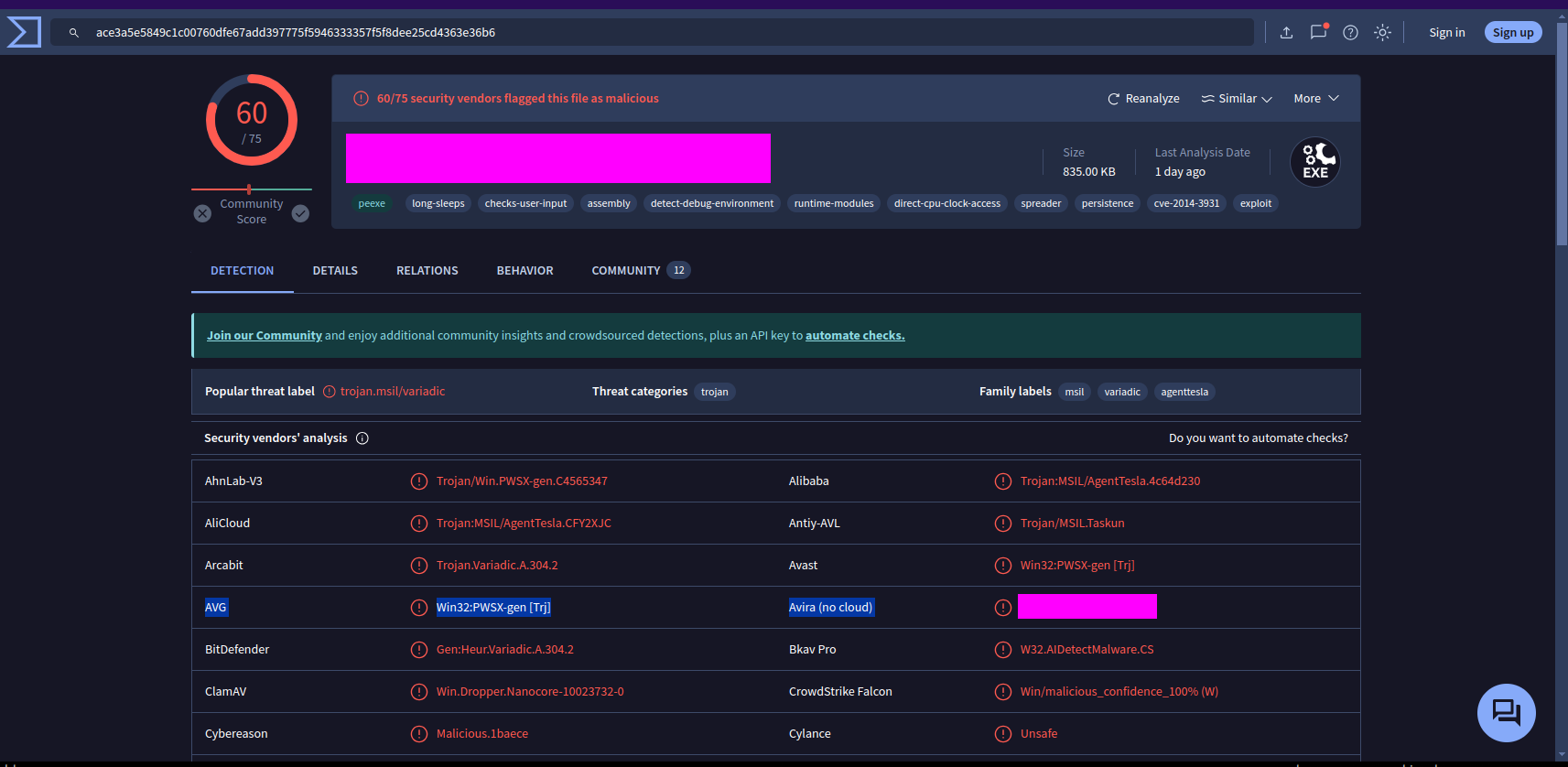
- 3: Using the hash, what is the number of detections of malbuster_1 in VirusTotal?
- 4: Based on VirusTotal detection, what is the malware signature of malbuster_2 according to Avira?
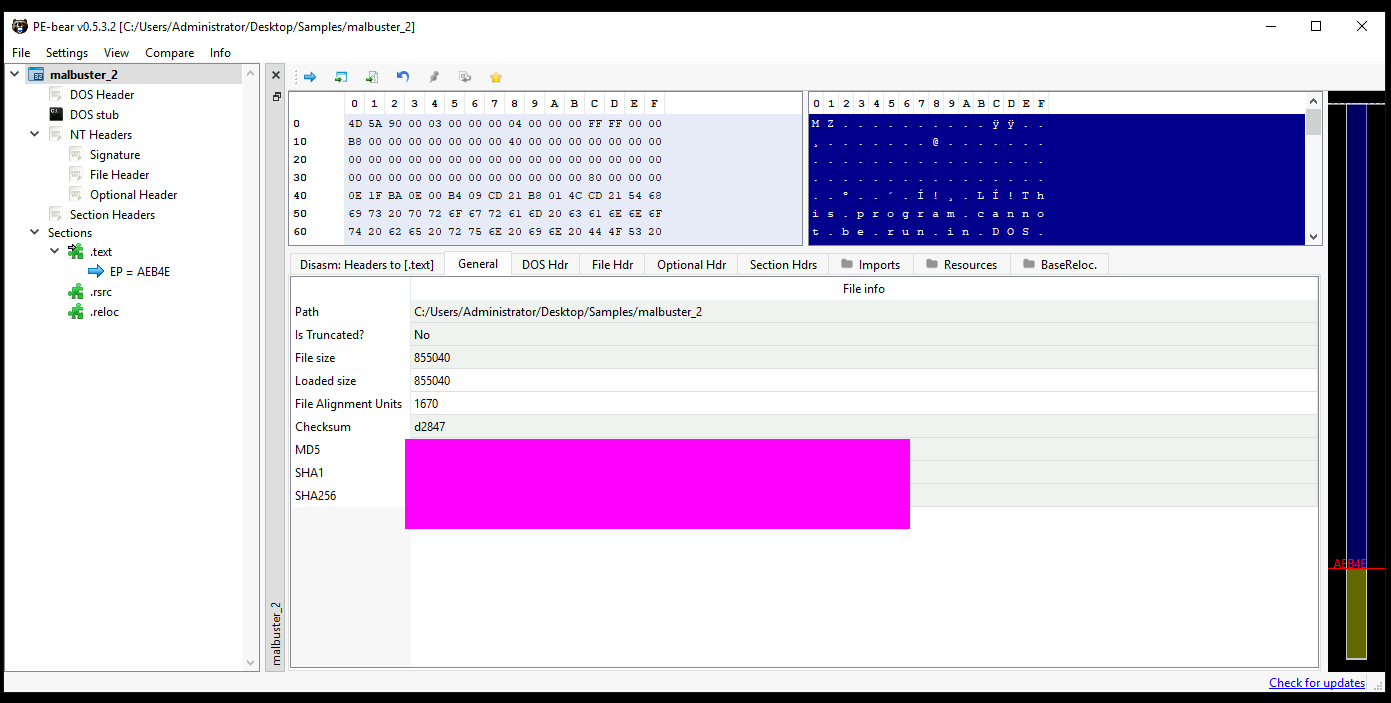
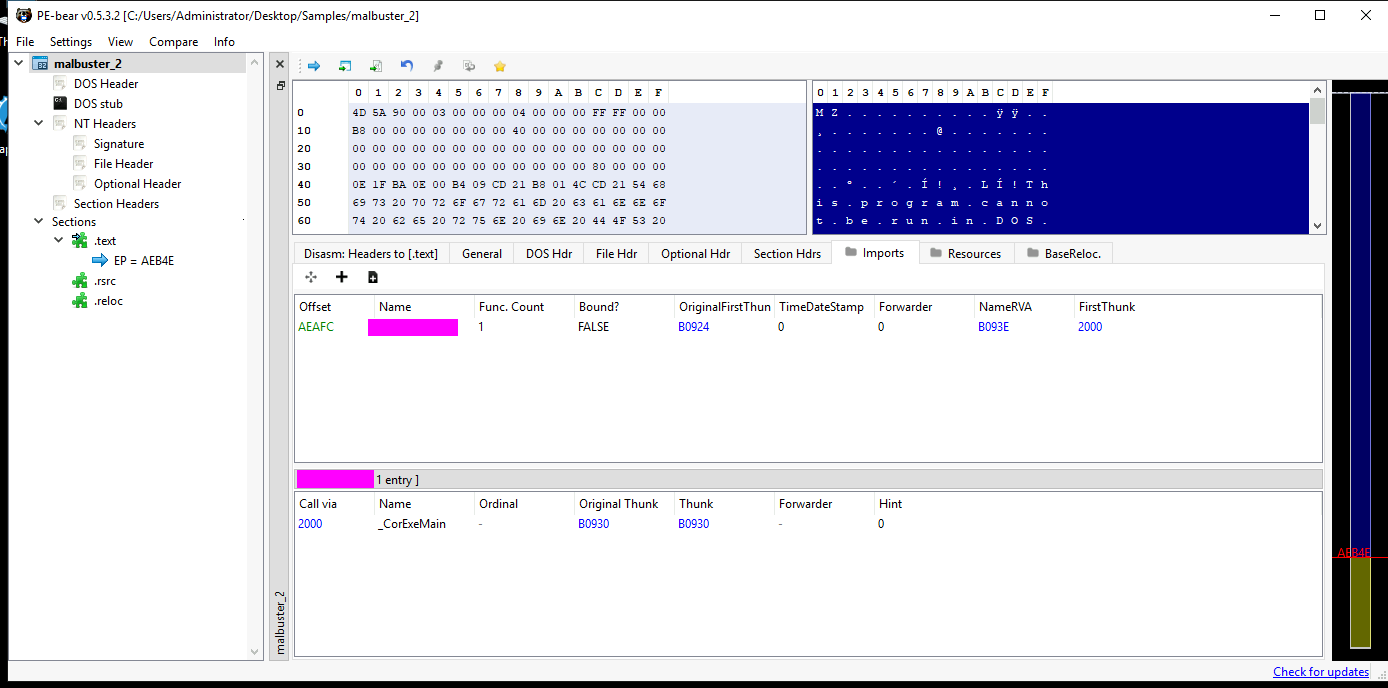
- 5: malbuster_2 imports the function _CorExeMain. From which DLL file does it import this function?
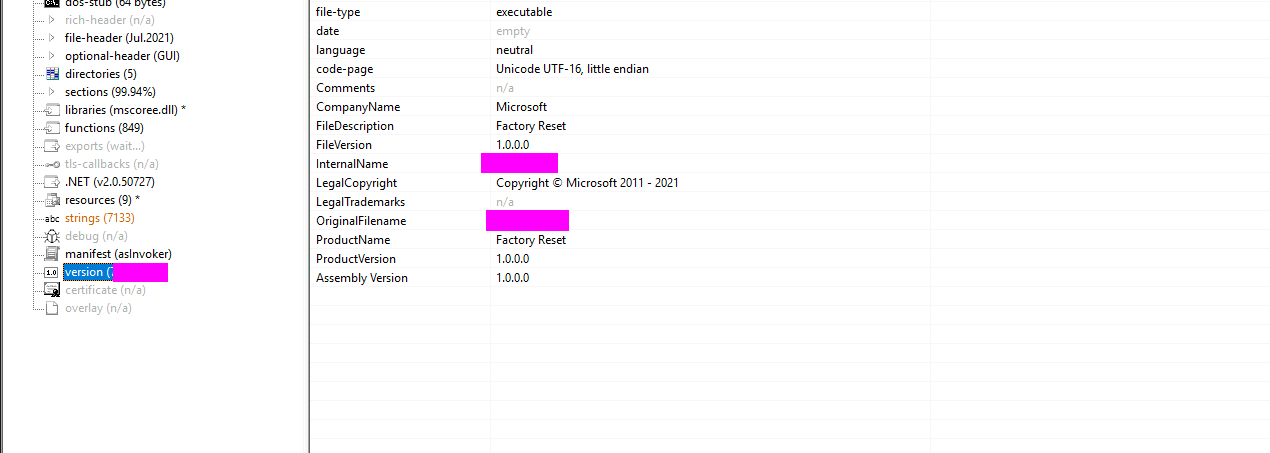
- 6: Based on the VS_VERSION_INFO header, what is the original name of malbuster_2?
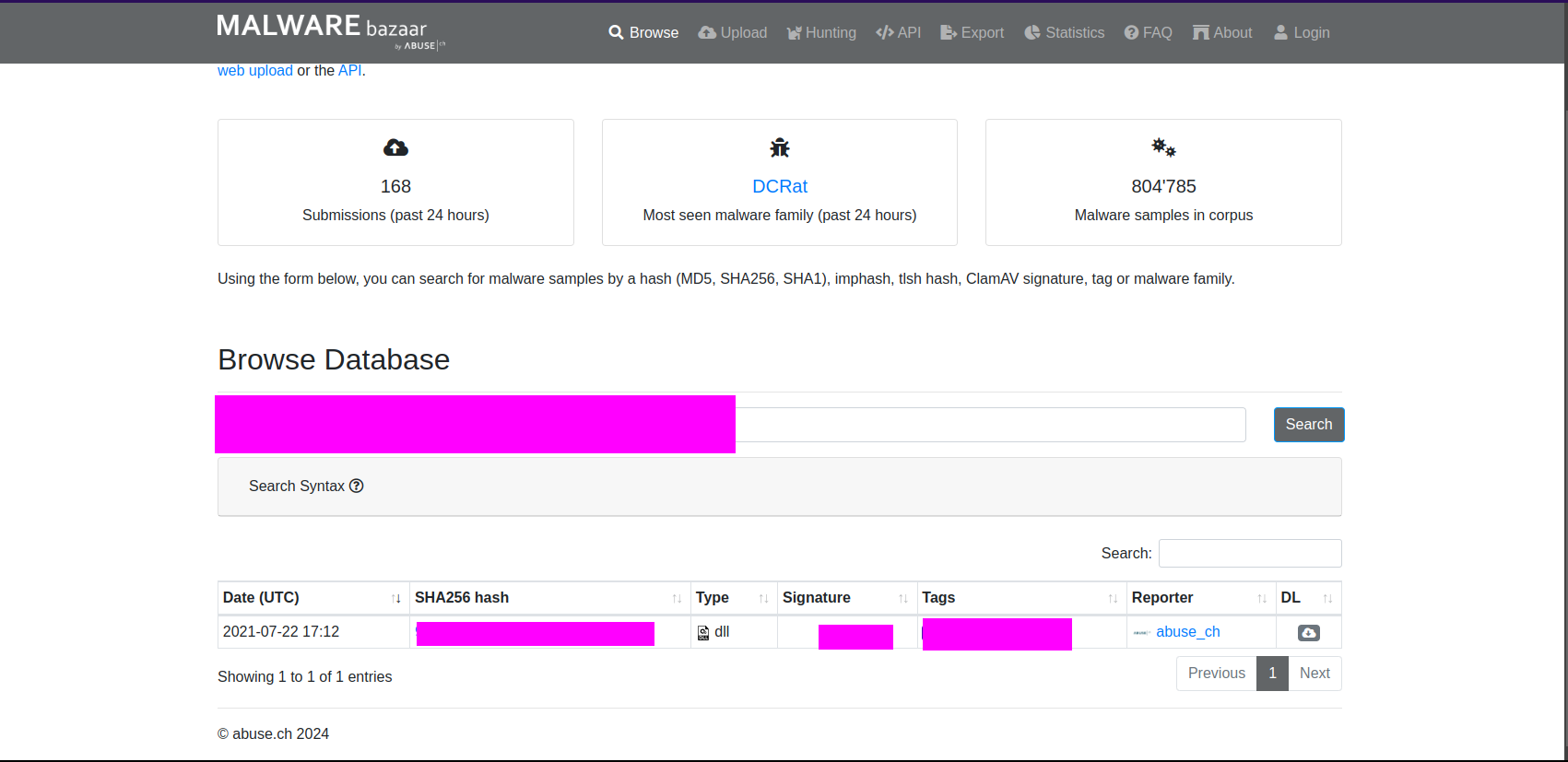
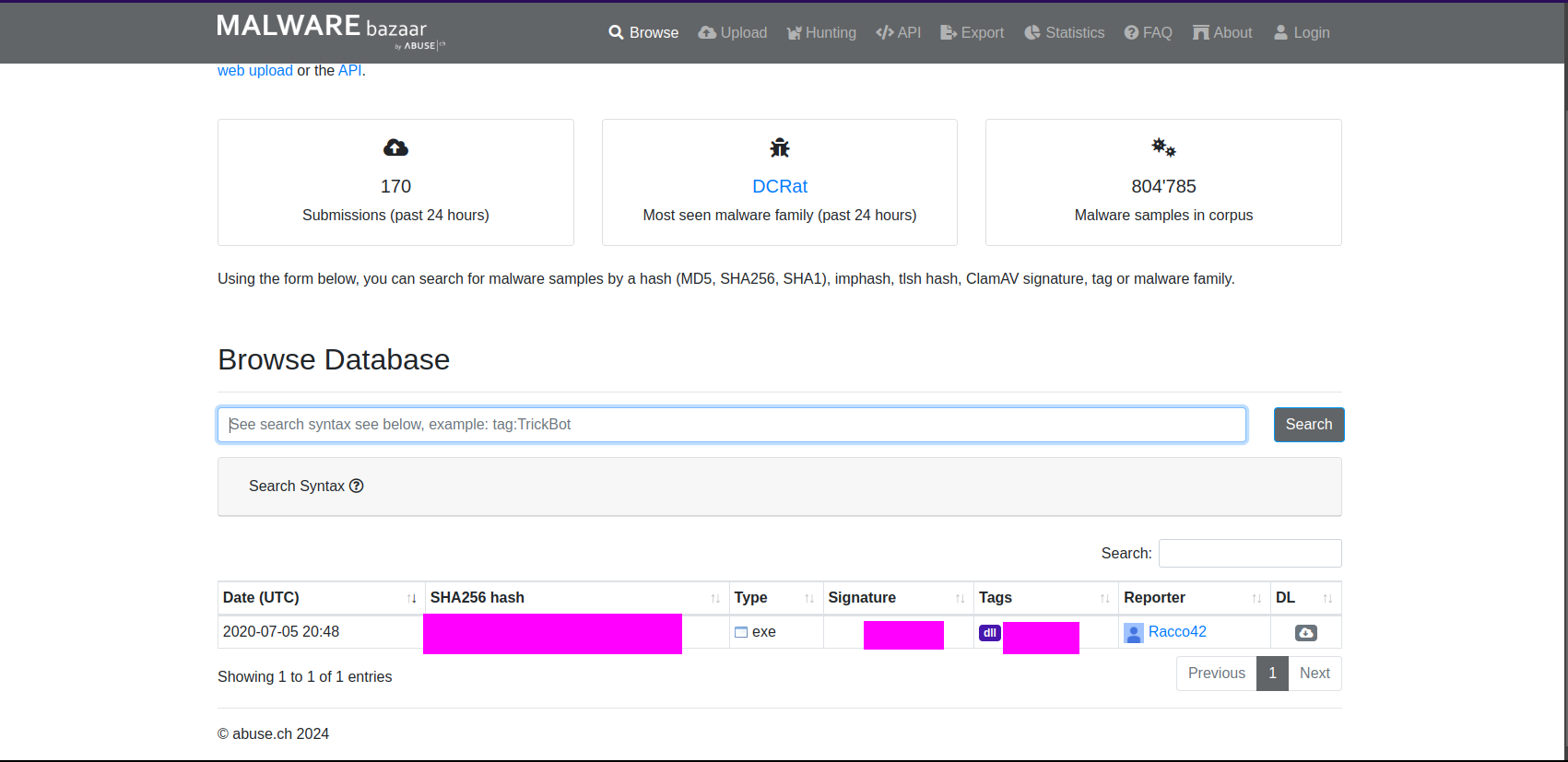
- 7: Using the hash of malbuster_3, what is its malware signature based on abuse.ch?
- 8: Using the hash of malbuster_4, what is its malware signature based on abuse.ch?
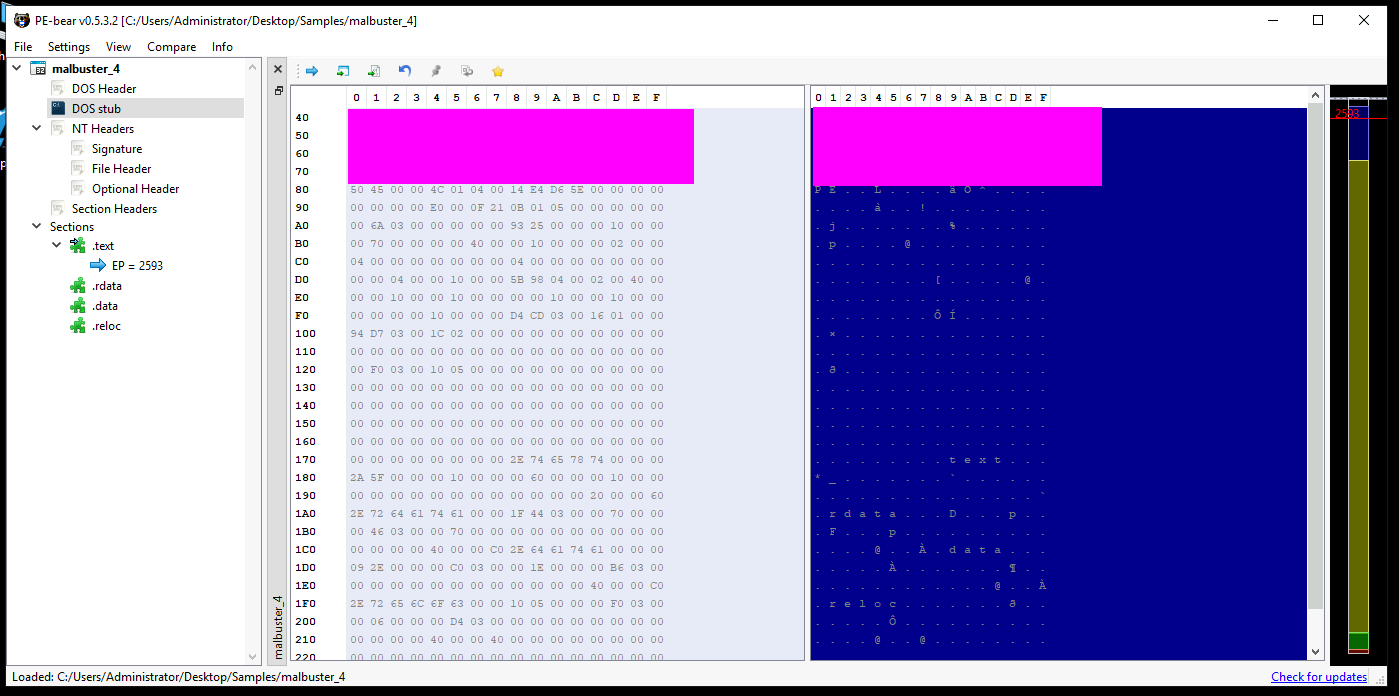
- 9: What is the message found in the DOS_STUB of malbuster_4?
- 10: malbuster_4 imports the function ShellExecuteA. From which DLL file does it import this function?
- To find this we can return to PE Bear and view the imports section. There are a lot of libraries but you can sift through until you find what you are looking for.
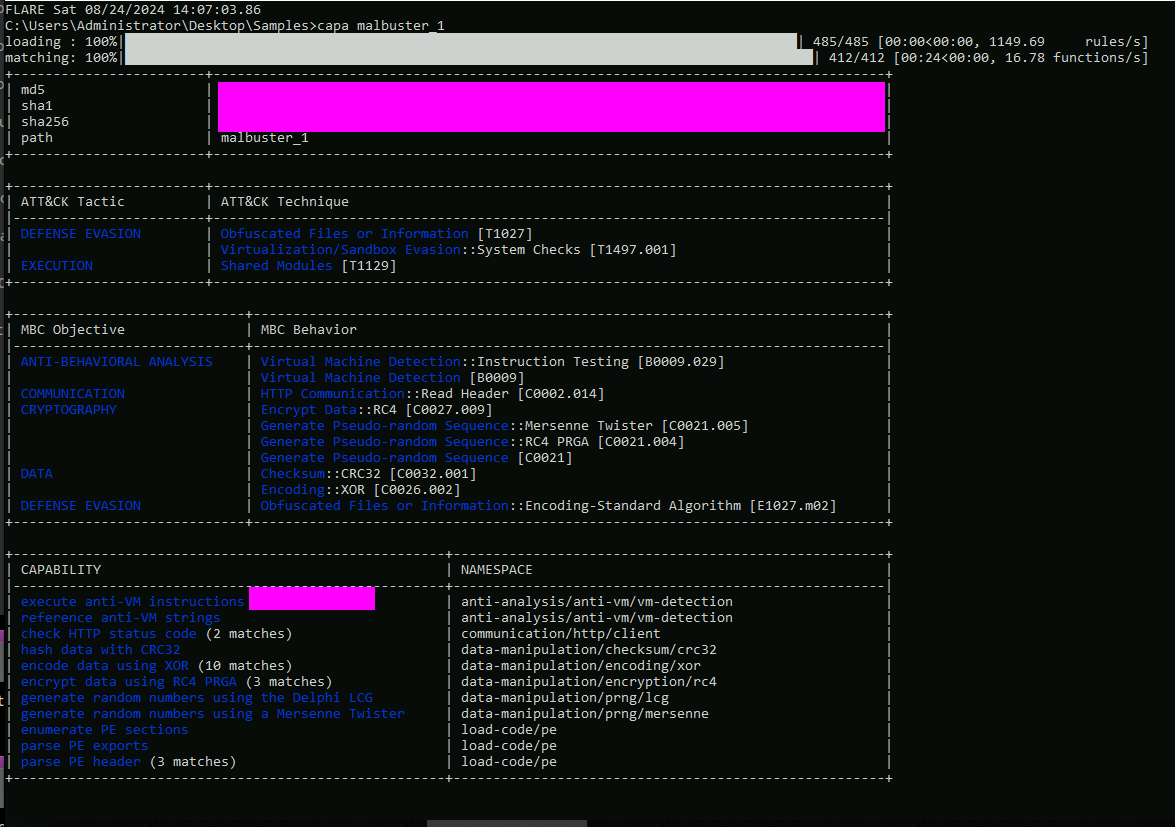
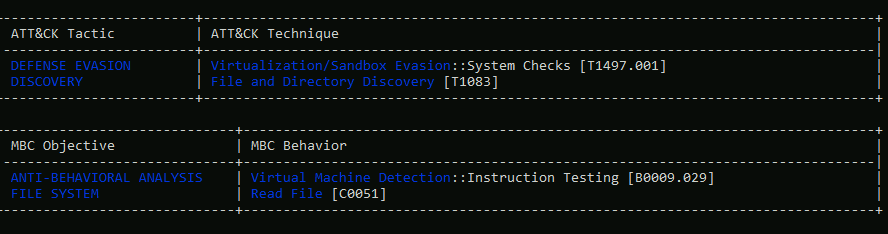
- 11: Using capa, how many anti-VM instructions were identified in malbuster_1?
- 12: Using capa, which binary can log keystrokes?
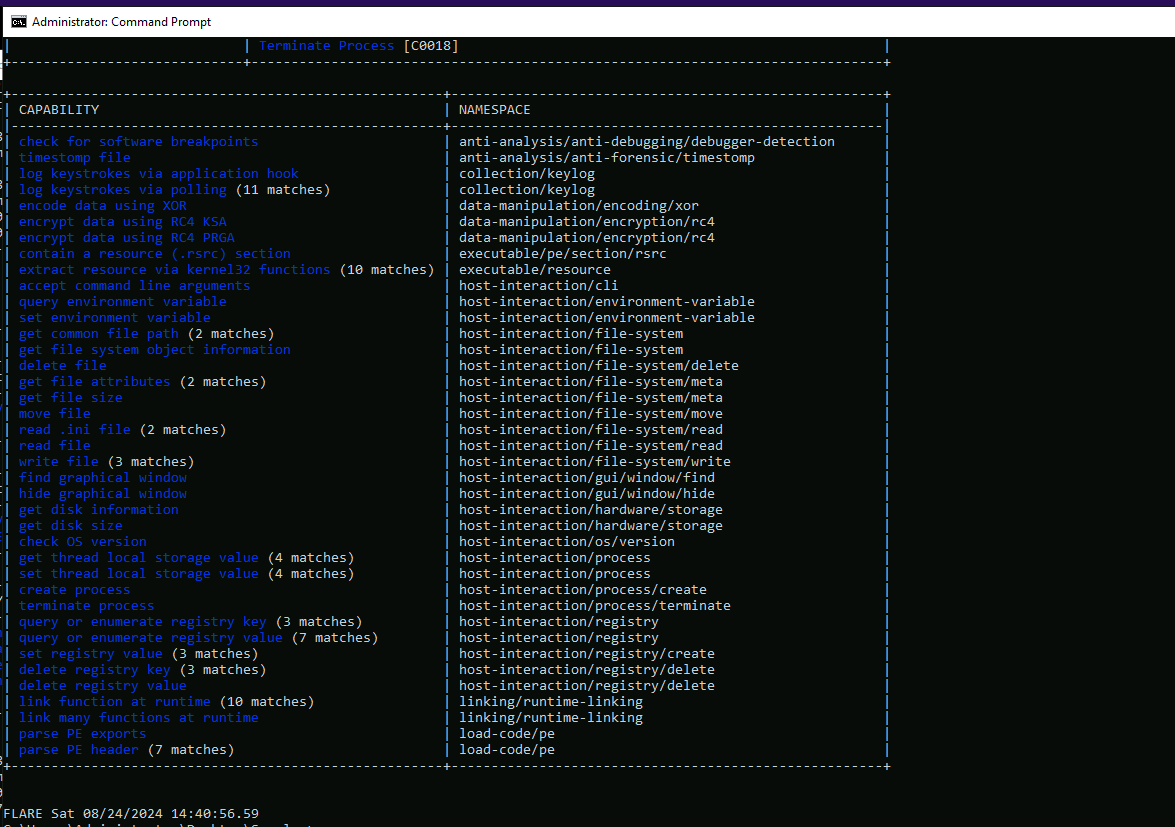
- 13: Using capa, what is the MITRE ID of the DISCOVERY technique used by malbuster_4?
Conclusion:
Just like that the room is solved, this was a pretty simple malware challenge that can help people get familar with the unique tools used in malware analysis.